RADIUS Server
Introduction
In the previous sessions of our MCSA Full Course, we explored how to configure a VPN server and set up NPS (Network Policy Server). Today, in Day 39, we dive into the RADIUS Server — a crucial component for managing authentication, authorization, and accounting (AAA) across multiple VPN servers.
If you’re an IT professional or a beginner, understanding RADIUS is essential because it helps you centralize and secure remote access in enterprise environments.
What is a RADIUS Server?
RADIUS (Remote Authentication Dial-In User Service) is a networking protocol used to provide:
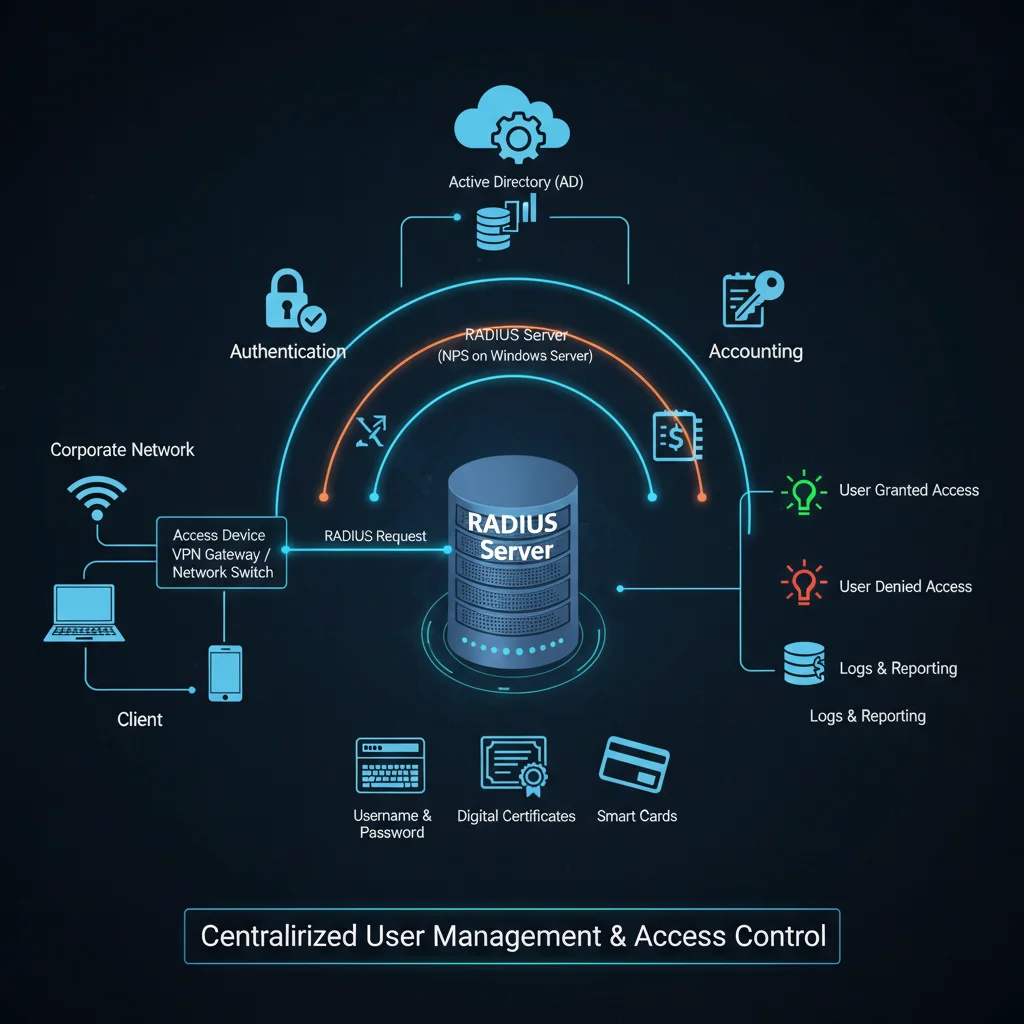
- Authentication – Verifying user identity.
- Authorization – Granting appropriate access rights.
- Accounting – Tracking usage, session duration, and logs.
In Windows Server, RADIUS is implemented through NPS (Network Policy Server). This allows administrators to enforce access policies and integrate with Active Directory for centralized user management.
Why Do We Need a RADIUS Server?
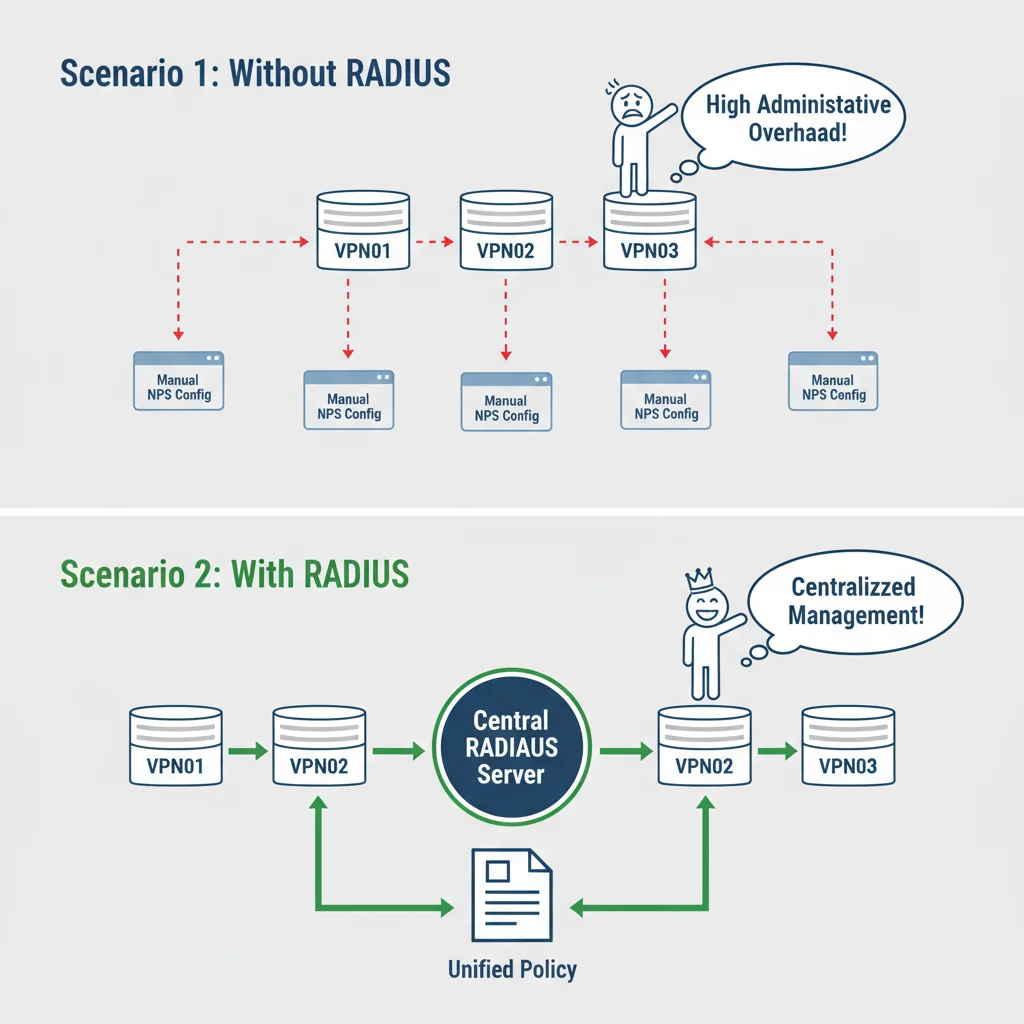
When you have only one VPN server, you can configure policies directly on that server. But in real-world enterprises, there are often multiple VPN servers.
Without RADIUS:
- You would have to configure policies on each server individually.
- Updating or troubleshooting becomes time-consuming and error-prone.
With RADIUS:
- All VPN servers connect to a centralized server.
- Policies are created once and applied everywhere.
- User authentication is checked against Active Directory centrally.
This simplifies management, improves scalability, and ensures consistent security policies across the organization.
How RADIUS Works (Step by Step)
- Client Connection:
A remote user tries to connect to the company’s network via VPN. - Request Forwarded:
The VPN server forwards the authentication request to the RADIUS server. - Policy Validation:
The RADIUS server checks the defined NPS policies, authentication methods, and user group memberships. - Active Directory Integration:
Credentials are verified with the domain controller. - Response:
Based on the result, the RADIUS server tells the VPN whether to allow, deny, or log the connection.
This setup ensures that every VPN server is consistent, and user access can be managed centrally.
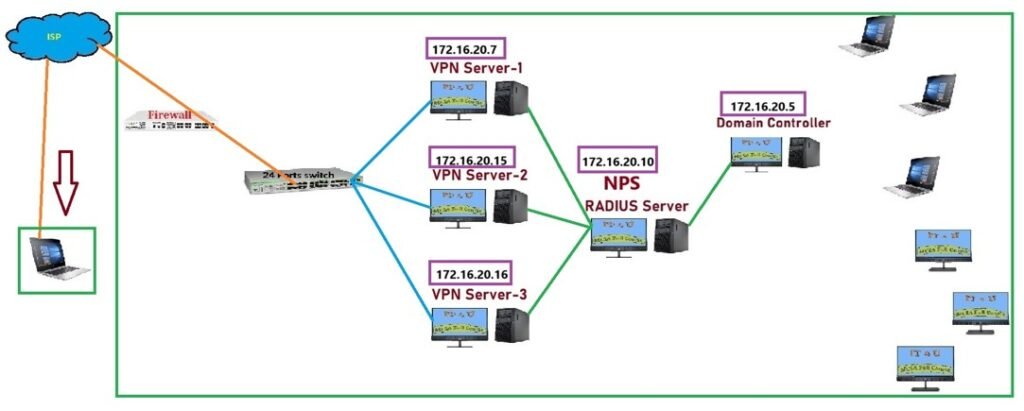
Real-World Scenario
Imagine a company with three VPN servers: VPN01, VPN02, and VPN03.
- Without RADIUS: Each VPN needs manual NPS configuration.
- With RADIUS: All three servers forward requests to the RADIUS server, which applies the same policies to all connections.
This way, admins only need to manage one NPS configuration instead of three.
Key Features of RADIUS Server
- ✅ Centralized Policy Control – One place to define access rules.
- ✅ Active Directory Integration – Works seamlessly with AD users and groups.
- ✅ Supports Multiple Devices – Not just VPNs, but also routers, switches, firewalls, and wireless access points.
- ✅ Scalable Solution – Easy to add new VPN or wireless servers.
- ✅ Enhanced Security – Uses shared secrets and encryption to secure communication between servers.
Benefits of Using RADIUS
- Consistency: The same rules apply across all VPN servers.
- Security: Protects against unauthorized access with centralized AAA.
- Efficiency: Reduces admin effort by managing policies in one place.
- Flexibility: Works with different authentication methods like passwords, certificates, and smart cards.
- Accounting Logs: Generates useful reports for monitoring and troubleshooting.
FAQ – RADIUS Server
Q1: What is a RADIUS Server in simple terms?
A RADIUS server is a system that verifies who you are, decides what access you get, and keeps a record of your activity when connecting remotely to a network.
Q2: How is RADIUS different from NPS?
RADIUS is the protocol, while NPS (Network Policy Server) is Microsoft’s implementation of that protocol in Windows Server.
Q3: Why should I use a RADIUS server for VPNs?
It centralizes authentication and policy management, especially useful when you have multiple VPN servers.
Q4: Can RADIUS integrate with Active Directory?
Yes. RADIUS uses AD credentials to validate users and apply group-based access rules.
Q5: What happens if the RADIUS server goes down?
If no backup RADIUS server is configured, VPN authentication may fail. That’s why enterprises often deploy multiple RADIUS servers for redundancy.
Q6: Can I use RADIUS with non-Microsoft devices?
Yes. Any device that supports the RADIUS protocol — such as routers, switches, and firewalls — can use it.
Q7: Does RADIUS log user activity?
Yes. It records login attempts, session times, data usage, and disconnection reasons, making it useful for auditing.
Conclusion
The RADIUS Server is a cornerstone of enterprise security and scalability. It ensures that authentication, authorization, and accounting are managed centrally and consistently across all VPN and network devices.
By integrating with Active Directory, RADIUS allows organizations to secure their environments with minimal manual effort, while providing flexibility and detailed logging.
💡 What do you think about RADIUS in enterprise environments?
Share your thoughts in the comments and don’t forget to subscribe to IT4U for more tutorials in this MCSA Full Course.









Add comment