VPN (Virtual Private Network)
Introduction
In today’s digital world, network security is one of the top priorities for organizations and individuals. Whether you’re working remotely, traveling, or accessing corporate resources, a secure connection is essential. That’s where a VPN (Virtual Private Network) comes into play.

In this lesson from our MCSA Full Course (Day 37), we’ll explore VPNs in detail—what they are, how they work, their types, the most commonly used protocols, and why they’re important for businesses and IT professionals.
What is a VPN?
A VPN (Virtual Private Network) is a technology that creates a secure and encrypted connection between your device and the internet. This means the data you send or receive is protected from hackers, trackers, and other malicious activities.

When you connect via a VPN:
- Your device communicates securely with the internet.
- Data is encrypted before transmission.
- Hackers or intruders cannot easily track or intercept your information.
Types of VPN
There are two main types of VPNs used in organizations and by individuals:
1. Remote Access VPN
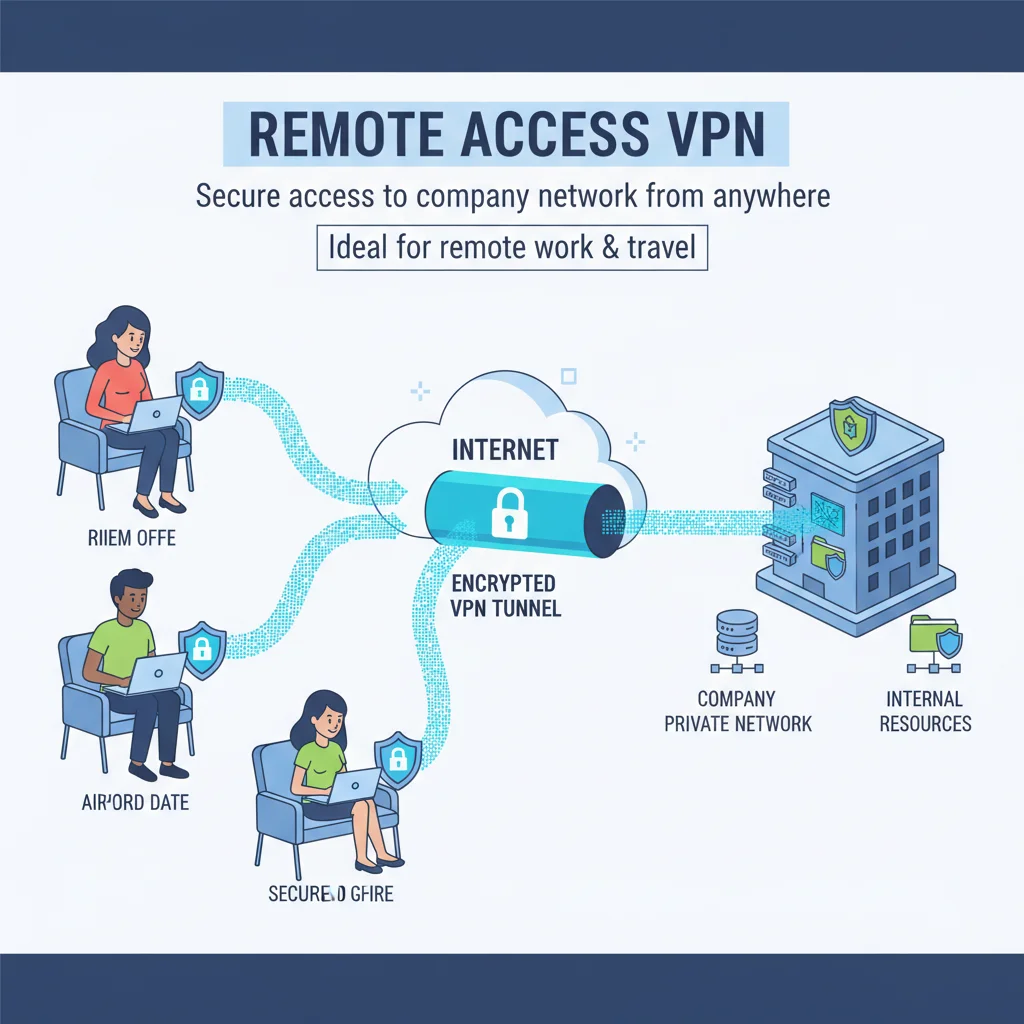
- Used by employees or individuals working from home or traveling.
- Provides secure access to the company’s private network from any location.
- Common in modern work-from-home scenarios.
2. Site-to-Site VPN
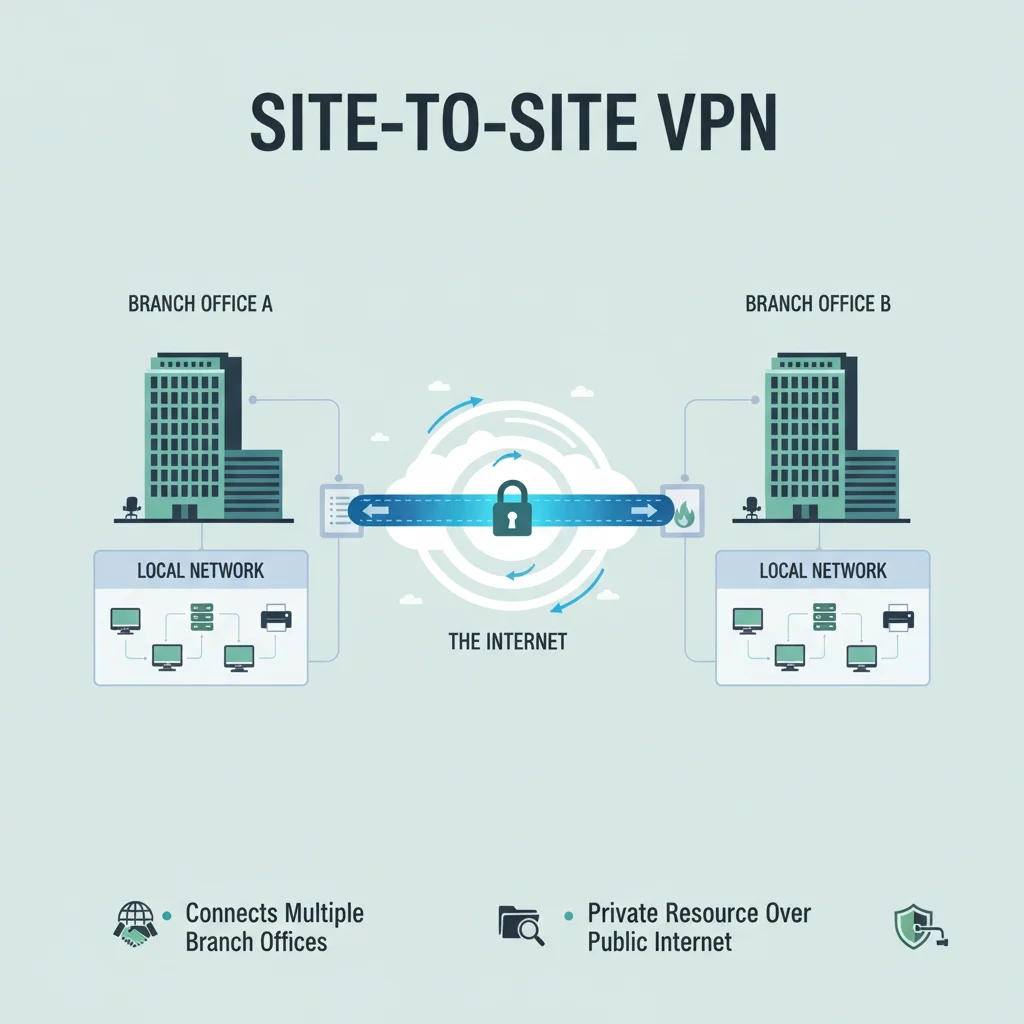
- Connects two or more networks securely over the internet.
- Commonly used by businesses with multiple branch offices.
- Enables sharing of resources across different office locations.
VPN Protocols
VPNs operate using protocols, which are sets of rules that define how data is transmitted and secured. Each protocol has its strengths and weaknesses.
🔹 PPTP (Point-to-Point Tunneling Protocol)
- One of the earliest VPN protocols.
- Easy to set up and supported by most operating systems.
- Weakness: Not as secure as modern alternatives and can be compromised.
- Still used in scenarios where basic encryption is enough.
🔹 L2TP/IPSec (Layer 2 Tunneling Protocol with Internet Protocol Security)
- Combines two protocols for stronger encryption.
- Provides high-level security for data transmission.
- Widely used in site-to-site VPNs.
🔹 SSTP (Secure Socket Tunneling Protocol)
- Developed by Microsoft.
- Provides SSL/TLS encryption for secure connections.
- Works mainly on Windows devices.
🔹 OpenVPN
- Open-source and widely regarded as one of the most secure VPN protocols.
- Uses SSL/TLS encryption.
- Highly configurable and supported on multiple platforms including Windows, Linux, macOS, and Android.
Why Do We Need a VPN?

VPNs are critical because they:
- Protect against hackers: Prevent outsiders from intercepting your network traffic.
- Enable remote work: Employees can access company servers securely from anywhere.
- Secure public Wi-Fi usage: Prevents data theft when connected to open networks.
- Ensure privacy: Your browsing activities remain private and less traceable.
For example, without a VPN, if an employee connects to public Wi-Fi, hackers can sniff or track their data. With a VPN, a secure tunnel is created, hiding the actual communication path.
Real-World Use Case of VPN
Consider a company with employees working from both office and home:
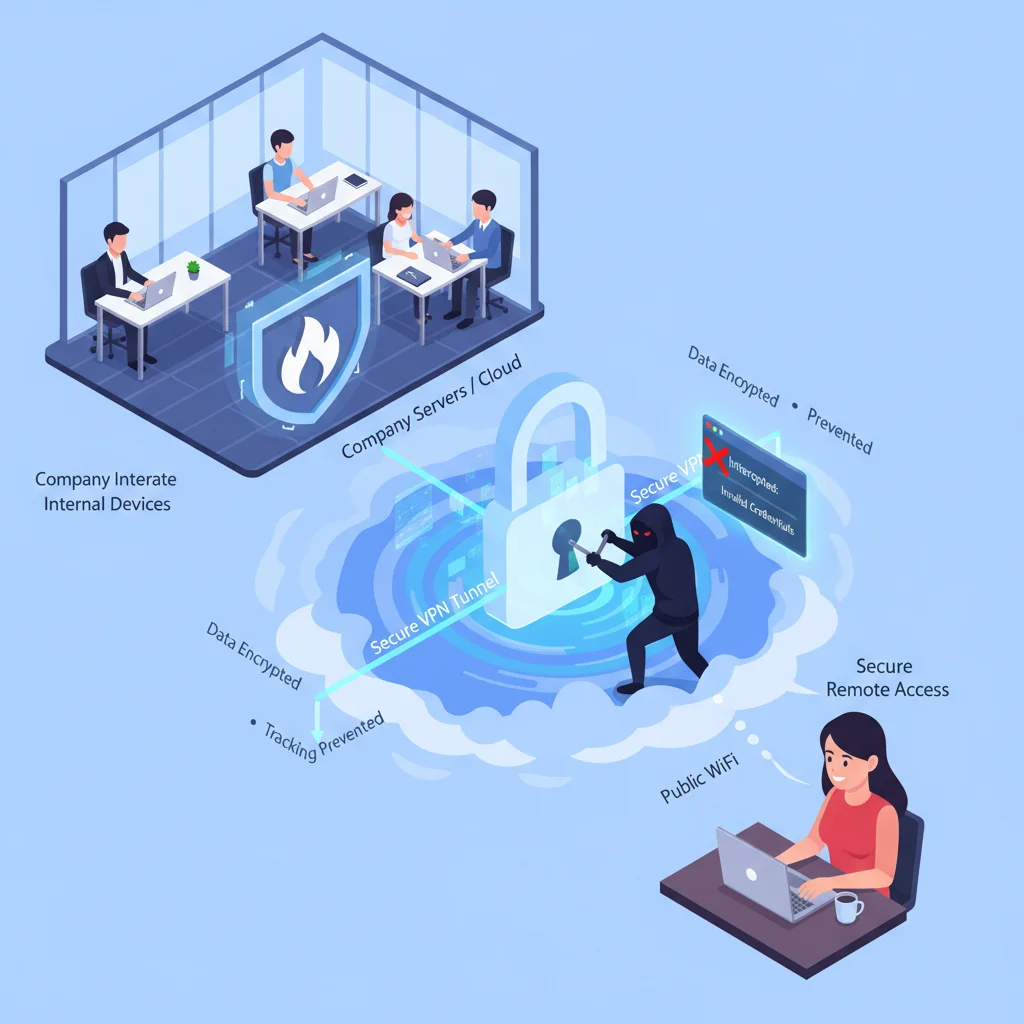
- Internal devices connect securely within the company’s firewall.
- A remote employee uses a VPN to access company servers.
- The VPN encrypts the connection, ensuring hackers cannot track or compromise the data flow.
Thus, even if the username and password were compromised, VPN adds another security layer through encryption and tunneling.
VPN Configuration (Windows Server Example)
In a Microsoft environment:
- A VPN server is set up with two NICs (network interface cards)—one for local LAN, another for public IP.
- Remote clients connect via VPN and receive IP addresses from a predefined pool.
- Once connected, they can securely access internal resources like file shares, printers, and servers.
This is exactly what we configure in the MCSA Full Course practical sessions.
Conclusion
VPNs are no longer optional—they are a necessity in today’s IT infrastructure. Whether you’re an IT professional, student, or business owner, understanding VPNs is crucial for ensuring secure connectivity.
👉 Stay tuned for upcoming lessons where we’ll cover advanced VPN protocols like OpenVPN and certificate-based authentication.
💡 What do you think about VPNs? Have you used them in your workplace? Share your thoughts in the comments below!
Frequently Asked Questions (FAQ)
Q1: What is the main purpose of a VPN?
A VPN secures your connection by encrypting data and protecting it from hackers or unauthorized tracking.
Q2: Which type of VPN is best for remote workers?
Remote Access VPN is best for individuals working from home or while traveling.
Q3: Is PPTP still safe to use?
PPTP is outdated and less secure. Modern protocols like L2TP/IPSec or OpenVPN are better choices.
Q4: What is the difference between VPN and firewall?
A firewall blocks unauthorized access, while a VPN creates a secure tunnel for safe communication.
Q5: Can VPNs be used on mobile devices?
Yes, VPNs can be configured on smartphones and tablets for secure internet browsing.
Q6: Does VPN slow down the internet?
Sometimes yes, due to encryption overhead, but modern VPNs are optimized to minimize speed loss.
Q7: What is the most secure VPN protocol?
OpenVPN is widely considered the most secure due to its strong encryption and flexibility.
VPN Interview Questions and Answers
Q1: What is a VPN?
A VPN (Virtual Private Network) is a technology that creates a secure and encrypted connection between your device and the internet.
Q2: Why is VPN important in today’s IT environment?
VPNs are essential for securing data, protecting user privacy, and enabling safe remote access to corporate resources.
Q3: What are the main types of VPN?
The two main types are Remote Access VPN and Site-to-Site VPN.
Q4: How does a Remote Access VPN work?
It allows individual users to securely connect to a private network from remote locations using an encrypted tunnel.
Q5: What is a Site-to-Site VPN?
A Site-to-Site VPN securely connects two or more networks (such as branch offices) over the internet.
Q6: What are common VPN protocols?
Common VPN protocols include PPTP, L2TP/IPSec, SSTP, and OpenVPN.
Q7: Which VPN protocol is most secure?
OpenVPN is considered the most secure because it uses SSL/TLS encryption and supports multiple platforms.
Q8: Does a VPN slow down internet speed?
Yes, sometimes VPNs reduce speed due to encryption overhead, but modern VPNs are optimized to minimize this impact.
Q9: Can VPNs be used on mobile devices?
Yes, VPN apps are available for Android, iOS, and other mobile platforms for secure browsing and data protection.
Q10: What is the difference between VPN and Firewall?
A firewall blocks unauthorized access, while a VPN creates a secure tunnel for encrypted communication.









Add comment